WordPress Security – 19 Steps to Lock Down Your Site

When it comes to WordPress security, there are a lot of things you can do to lock down your site to prevent hackers and vulnerabilities from affecting your ecommerce site or blog. The last thing you want to happen is to wake up one morning to discover your site in shambles. So today we are going to be sharing a lot of tips, strategies, and techniques you can use to better your WordPress security and stay protected.
If you’re a Kinsta client, you don’t need to worry about a lot of these, as we offer free hack fixes! But even with this guarantee, you should always follow the best security practices.
Is WordPress Secure?
The first question you’re probably wondering, is WordPress secure? For the most part, yes. However, WordPress usually gets a bad rap for being prone to security vulnerabilities and inherently not being a safe platform to use for a business. More often than not this is due to the fact that users keep following industry-proven security worst-practices.
Using outdated WordPress software, nulled plugins, poor system administration, credentials management, and lack of necessary Web and security knowledge among non-techie WordPress users keep hackers on top of their cyber-crime game. Even industry leaders don’t always use the best practices. Reuters was hacked because they were using an outdated version of WordPress.
Fundamentally, security is not about perfectly secure systems. Such a thing might well be impractical, or impossible to find and/or maintain. What security is though is risk reduction, not risk elimination. It’s about employing all the appropriate controls available to you, within reason, that allow you to improve your overall posture reducing the odds of making yourself a target, subsequently getting hacked. – WordPress Security Codex
Now, this is not to say vulnerabilities don’t exist. According to a Q3 2017 study by Sucuri, a multi-platform security company, WordPress continues to lead the infected websites they worked on (at 83%). This is up from 74% in 2016.

WordPress security vulnerabilities
WordPress powers over 40.0% of all websites on the internet, and with hundreds of thousands of theme and plugin combinations out there, it’s not surprising that vulnerabilities exist and are constantly being discovered. However, there is also a great community around the WordPress platform, to ensure these things get patched ASAP. As of 2021, the WordPress security team is made up of approximately 50 (up from 25 in 2017) experts including lead developers and security researchers — about half are employees of Automattic and a number work in the web security field.
WordPress Vulnerabilities
Check out some of the different types of WordPress security vulnerabilities below.
- Backdoors
- Pharma Hacks
- Brute-force Login Attempts
- Malicious Redirects
- Cross-site Scripting (XSS)
- Denial of Service
Backdoors
The aptly named backdoor vulnerability provides hackers with hidden passages bypassing security encryption to gain access to WordPress websites via abnormal methods – wp-Admin, SFTP, FTP, etc. Once exploited, backdoors enable hackers to wreak havoc on hosting servers with cross-site contamination attacks – compromising multiple sites hosted on the same server. In Q3 2017 Sucuri reported that backdoors continue to be one of the many post-hack actions attackers take, with 71% of the infected sites having some form of backdoor injection.

Malware family distribution
Backdoors are often encrypted to appear like legitimate WordPress system files, and make their way through to WordPress databases by exploiting weaknesses and bugs in outdated versions of the platform. The TimThumb fiasco was a prime example of backdoor vulnerability exploiting shady scripts and outdated software compromising millions of websites.
Fortunately, prevention and cure of this vulnerability is fairly simple. You can scan your WordPress site with tools like SiteCheck which can easily detect common backdoors. Two-factor authentication, blocking IPs, restricting admin access and preventing unauthorized execution of PHP files easily takes care of common backdoor threats, which we will go into more below. Canton Becker also has a great post on cleaning up the backdoor mess on your WordPress installations.
Pharma Hacks
The Pharma Hack exploit is used to insert rogue code in outdated versions of WordPress websites and plugins, causing search engines to return ads for pharmaceutical products when a compromised website searched for. The vulnerability is more of a spam menace than traditional malware, but gives search engines enough reason to block the site on accusations of distributing spam.
Moving parts of a Pharma Hack include backdoors in plugins and databases, which can be cleaned up following the instructions from this Sucuri blog. However, the exploits are often vicious variants of encrypted malicious injections hidden in databases and require a thorough clean-up process to fix the vulnerability. Nevertheless, you can easily prevent Pharma Hacks by using recommend WordPress hosting providers with up to date servers and regularly updating your WordPress installations, themes, and plugins. Hosts like Kinsta also offer free hack fixes.
Brute-force Login Attempts
Brute-force login attempts use automated scripts to exploit weak passwords and gain access to your site. Two-step authentication, limiting login attempts, monitoring unauthorized logins, blocking IPs and using strong passwords are some of the easiest and highly effective ways to prevent brute-force attacks. But unfortunately, a number of WordPress website owners fail to perform these security practices whereas hackers are easily able to compromise as much as 30,000 websites in a single day using brute-force attacks.
Malicious Redirects
Malicious redirects create backdoors in WordPress installations using FTP, SFTP, wp-admin, and other protocols and inject redirection codes into the website. The redirects are often placed in your .htaccess file and other WordPress core files in encoded forms, directing the web traffic to malicious sites. We will go through some ways you can prevent these in our WordPress security steps below.
Cross-Site Scripting (XSS)
Cross-Site Scripting (XSS) is when a malicious script is injected into a trusted website or application. The attacker uses this to send malicious code, typically browser-side scripts, to the end user without them knowing it. The purpose is usually to grab cookie or session data or perhaps even rewrite HTML on a page.
According to WordFence, Cross-Site Scripting vulnerabilities are the most common vulnerability found in WordPress plugins by a significant margin.
Denial of Service
Perhaps the most dangerous of them all, Denial of Service (DoS) vulnerability exploits errors and bugs in the code to overwhelm the memory of website operating systems. Hackers have compromised millions of websites and raked in millions of dollars by exploiting outdated and buggy versions of WordPress software with DoS attacks. Although financially motivated cybercriminals are less likely to target small companies, they tend to compromise outdated vulnerable websites in creating botnet chains to attack large businesses.
Even the latest versions of WordPress software cannot comprehensively defend against high-profile DoS attacks, but will at least help you to avoid getting caught in the crossfire between financial institutions and sophisticated cybercriminals. And don’t forget about October 21st, 2016. This was the day the internet went down due to a DNS DDoS attack. Read more about why it is important to use a premium DNS provider to increase your WordPress security.
WordPress Security Guide 2021
According to internet live stats over 100,000 websites are hacked every day. 😮 That’s why it’s so important to take some time and go through the following recommendations below on how to better harden your WordPress security.

WordPress sites hacked every day
We will make sure to keep this post up to date with relevant information as things change with the WordPress platform and new vulnerabilities emerge.
- Secure WordPress Hosting
- Use Latest PHP Version
- Clever Usernames and Passwords
- Latest Versions
- Lock Down WordPress Admin
- Two-Factor Authentication
- HTTPS – SSL Certificate
- Hardening wp-config.php
- Disable XML-RPC
- Hide WordPress Version
- HTTP Security Headers
- WordPress Security Plugins
- Database Security
- Secure Connections
- File and Server Permissions
- Disable Editing in Dashboard
- Prevent Hotlinking
- Always Take WordPress Backups
- DDoS Protection
1. Invest in Secure WordPress Hosting
When it comes to WordPress security, there is much more than just locking down your site, although we’ll give you the best recommendations on how to do that below. There is also web server-level security for which your WordPress host is responsible. We take security very seriously here at Kinsta and handle a lot of these issues for our clients.
It’s very important that you choose a host that you can trust with your business. Or if you are hosting WordPress on your own VPS, then you need to have the technical knowledge to do these things yourself. And to be honest, trying to be a sysadmin to save $20/month is a bad idea.
Secure WordPress hosting
Server hardening is the key to maintaining a thoroughly-secure WordPress environment. It takes multiple layers of hardware and software level security measures to ensure the IT infrastructure hosting WordPress sites is capable of defending against sophisticated threats, both physical and virtual.
For this reason, servers hosting WordPress should be updated with the latest operating system and (security) software as well as thoroughly tested and scanned for vulnerabilities and malware. A good example of this is when Kinsta had to patch NGINX for OpenSSL security vulnerabilities that were discovered.
Server-level firewalls and intrusion detection systems should be in place before installing WordPress on the server to keep it well-protected even during the WordPress installation and website construction phases. However, every software installed on the machine intended to protect WordPress content should be compatible with the latest database management systems to maintain optimal performance. The server should also be configured to use secure networking and file transfer encryption protocols (such as SFTP instead of FTP) to hide away sensitive content from malicious intruders.
Here at Kinsta, we use Google Cloud Platform’s fastest servers and premium tier network for all of our WordPress customers to ensure a fast and secure WordPress hosting experience. A big advantage of this is that it is built on a security model that has been built upon over the course of 15 years, and currently secures products and services like Gmail, Search, etc. Google currently employs more than 500 full-time security professionals. All sites on Kinsta are also protected by our free Cloudflare integration, which includes a secure enterprise-level firewall as well as free DDoS protection.
Kinsta also uses Linux containers (LXC), and LXD to orchestrate them, on top of Google Cloud Platform which enables us to completely isolate not just each account, but each separate WordPress site. Security is built into our architecture from the beginning and this is a much more secure method than offered by other competitors.
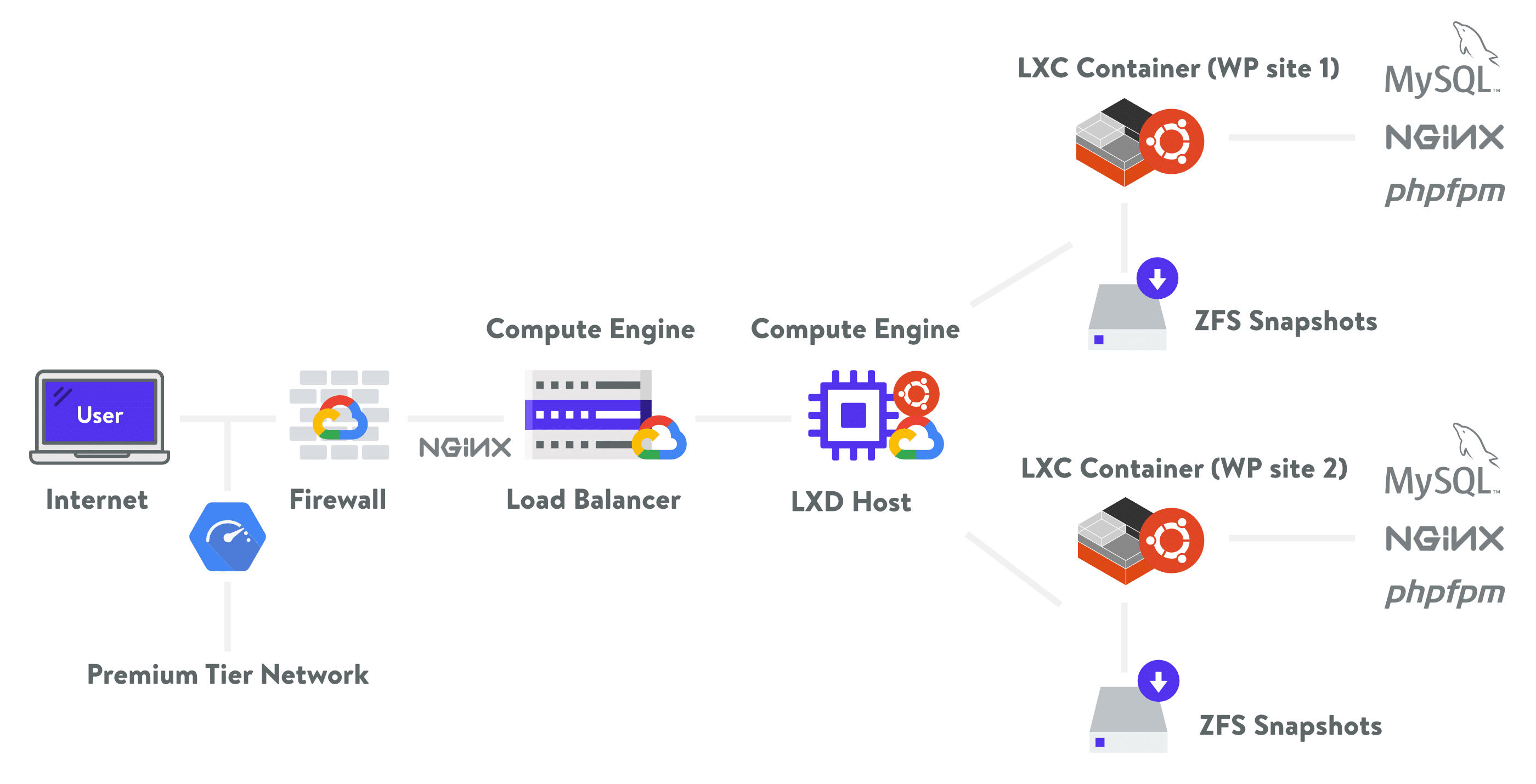
Kinsta hosting architecture.
2. Use Latest PHP Version
PHP is the backbone of your WordPress site and so using the latest version on your server is very important. Each major release of PHP is typically fully supported for two years after its release. During that time, bugs and security issues are fixed and patch on a regular basis. As of right now, anyone running on version PHP 7.1 or below no longer has security support and are exposed to unpatched security vulnerabilities.

Supported PHP Versions
And guess what? According to the official WordPress Stats
